Principles of Zero Trust security – What is Zero Trust, Why your business needs it and How to get started
“Zero Trust” refers to a security framework where every user or device must be authenticated and validated before being granted access to any business system, application, or asset(s). You might also hear it referred to as “perimeter-less security.”
Forrester coined the term in 2009. The concept goes back further than that.
Today, we see a heightened urgency to implement Zero Trust environments. The urgency derives from several factors:
- Increased cloud service usage outside of network perimeters.
- Remote work in a global economy obliterated the idea of network perimeter.
- Expanding “hybrid” work practices.
Perhaps the biggest reason – COVID-19 accelerated the need for cloud applications to keep people connected, productive, and communicating.
Related to the increased surge in remote work, 2020 saw a dramatic rise in cyberattacks, especially ransomware – making security a priority for organizations around the world.
Although interest in the practice has increased since March of 2020, our services teams have been encouraging customers to adopt and implement Zero Trust policies for their organizations for several years now.
What is needed to complete the shift to Zero Trust? It depends on an organization’s current network and cybersecurity posture.
This article aims to provide a solid foundation for getting started in the adoption of Zero Trust security.
What is Zero Trust security?
Zero Trust security refers to a continuously evolving set of cybersecurity standards that shift defenses from traditional static, network-based perimeters to focus on users (your people), assets (where your information and data live), and resources (tools used to protect your information).
The National Institute of Standards and Technology (NIST), a division of the U.S. Department of Commerce, defines Zero Trust in its document SP 800-207 as follows:
“Zero trust (ZT) provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised. Zero trust architecture (ZTA) is an enterprise’s cybersecurity plan that utilizes zero trust concepts and encompasses component relationships, workflow planning, and access policies. Therefore, a zero trust enterprise is the network infrastructure (physical and virtual) and operational policies that are in place for an enterprise as a product of a zero trust architecture plan.”
A lot of Zero Trust conversation often focuses on the technology. While technology is essential, we also reinforce the essential need to implement operational policies, such as well-defined password policies, as part of the effort. People play as big a role, if not bigger, in data and device security.
You can read more about password security in our article, "Solve password sprawl with password management."
Basic principles of Zero Trust
Zero Trust involves many elements and details. These can be expressed as the following principles.
Verify all, trust none. Traditional network security takes a view that a secured perimeter exists and any devices within that perimeter can be trusted. The Zero Trust approach recognizes that with remote and hybrid workforces, cloud computing, and cloud and “as-a-service” applications – not to mention smart and mobile devices, cloud printing, and more, traditional perimeters do not exist. As a result, no devices should be considered trusted, even within an established network perimeter.
Continual validation. To ensure only authorized, validated individuals are accessing data, systems must validate access always, all the time, for all resources.
Be prepared for a breach. A common saying today is not if a breach will occur, but when. Breaches can occur as a result of an external attack or internal accident (or truthfully, mal-intent too). A strong security posture aims to minimize the damage done with policies and technologies.
Monitor, measure, and improve. Data like network traffic, access requests, and current asset security practices should be collected, tracked, and measured for insight into ways to improve the overall security posture for the best possible response.
What is a Zero Trust architecture?
The NIST 800-207 standard provides a device/system agnostic framework for building a Zero Trust posture.
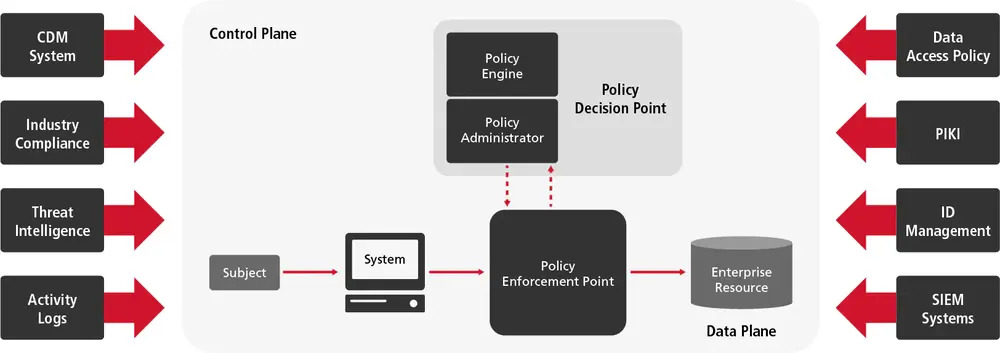
This is generally recognized as the standard for not only governmental entities, but private businesses as well, with validation from a variety of resources including government stakeholders and commercial businesses, as well as security vendors.
How Zero Trust works
Zero Trust relies on a multi-layered approach. With the traditional perimeter gone, the “trust but verify” paradigm is also gone, replaced by verify-verify-verify.
Technologies include:
- Multi-factor authentication
- Advanced endpoint protection
- Event isolation technologies like RansomCare
- Data encryption
- Identity management and protection
- Secured messaging
- Asset validation prior to connection
We would also add user education and training, specifically in the handling of email, hard copy data, and device usage in remote environments. Many organizations turn to Managed Security Services to support the best security posture, customized to their need.
One key element of Zero Trust deployments is the need for automation. Your defensive posture needs to continuously vet and enforce policies requires real-time visibility into all user and application identity attributes.
Different stages of the Zero Trust model
Most organizations are at different stages along the journey to a fully implemented Zero Trust deployment. The stages can be viewed as follows, understanding that in each one there is a spectrum of practice and progress.
Just getting started
In this stage, an organization’s cybersecurity posture most resembles the traditional static network defense.
- Devices and users with an on-premises identity (in the network) are considered safe.
- Limited rules and single-sign-on (SSO) are employed.
- The business has limited visibility to device compliance, logins, and usage of cloud environments.
- Broader risk exposure due to flat network infrastructure.
Improved defensive posture
With the Zero Trust journey begun, progress is visible.
- Access policies and enhanced hybrid identity practices create gates that must be passed to access data, networks, and applications.
- Well-defined IT security policies ensure devices are registered and compliant.
- Network segmentation and cloud threat protection have been implemented.
- Analytics practices are in place to assess user behavior and inform a proactive posture on threat identification.
An active Zero Trust environment
By this stage, organizations can measure the results of the improvements and automation enables real-time response.
- Real-time analytics together with cloud identity create dynamic gating to networks, applications, and data.
- Automated security policy makes data access decisions.
- Encryption secures data and every access is tracked.
- Threat detection and response are automated.
- All trust policies have been removed from the network, replaced with micro-segmentation, encryption, and micro cloud perimeters.
How to implement Zero Trust security in your organization
A Zero Trust implementation needs to address six general areas:
- Identities
- Devices
- Applications
- Infrastructure
- Network
- Data
For each of these, an organization needs technology, well-defined policy, and a way to engage users to encourage them to follow best practices.
Applications like Microsoft 365™ offer security features that meet Zero Trust principles. A breach isolation technology like RansomCare addresses the “Be prepared for breach” principle. And applications like Streamline NX can simplify managing device security.
The speed with which you research and implement the different factors really depends on your urgency. For organizations with an urgent need and that need to expedite their journey, a third-party IT services firm may help.

Source: RICOH USA
